Access Control Policy Template Iso 27001 - 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring An access control policy defines how your organization manages user access to systems, data, and applications. Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring
Risk assessment24/7 soc 2 monitoring An access control policy defines how your organization manages user access to systems, data, and applications. Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month 10k+ visitors in the past month
Risk assessment24/7 soc 2 monitoring An access control policy defines how your organization manages user access to systems, data, and applications. 10k+ visitors in the past month 10k+ visitors in the past month Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. Risk assessment24/7 soc 2 monitoring
ISO 270012022 ISMS Access Control Policy Template ISO Templates
10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month Iso 27001 is a widely used security standard that lays out how to build an effective information security management system.
ISO 270012022 ISMS Access Control Policy Template ISO Templates
Risk assessment24/7 soc 2 monitoring Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. An access control policy defines how your organization manages user access to systems, data, and applications.
ISO 270012022 ISMS Access Control Policy Template ISO Templates
Risk assessment24/7 soc 2 monitoring Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. 10k+ visitors in the past month An access control policy defines how your organization manages user access to systems, data, and applications. Risk assessment24/7 soc 2 monitoring
ISO 27001 Access Control Policy Ultimate Guide [+ template]
Risk assessment24/7 soc 2 monitoring Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month
ISO 270012022 ISMS Access Control Policy Template ISO Templates
10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. An access control policy defines how your organization manages user access to systems, data, and applications.
ISO 27001 Access Control Policy Template, Fulfill Control 5.15
Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month An access control policy defines how your organization manages user access to systems, data, and applications.
Iso 27001 Access Control Policy Template Template 1 Resume Examples
Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. An access control policy defines how your organization manages user access to systems, data, and applications. 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month
ISO 270012022 ISMS Access Control Policy Template ISO Templates
An access control policy defines how your organization manages user access to systems, data, and applications. 10k+ visitors in the past month 10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring Risk assessment24/7 soc 2 monitoring
ISO 27001 Access Control Policy Ultimate Guide [+ template]
Risk assessment24/7 soc 2 monitoring Risk assessment24/7 soc 2 monitoring An access control policy defines how your organization manages user access to systems, data, and applications. 10k+ visitors in the past month 10k+ visitors in the past month
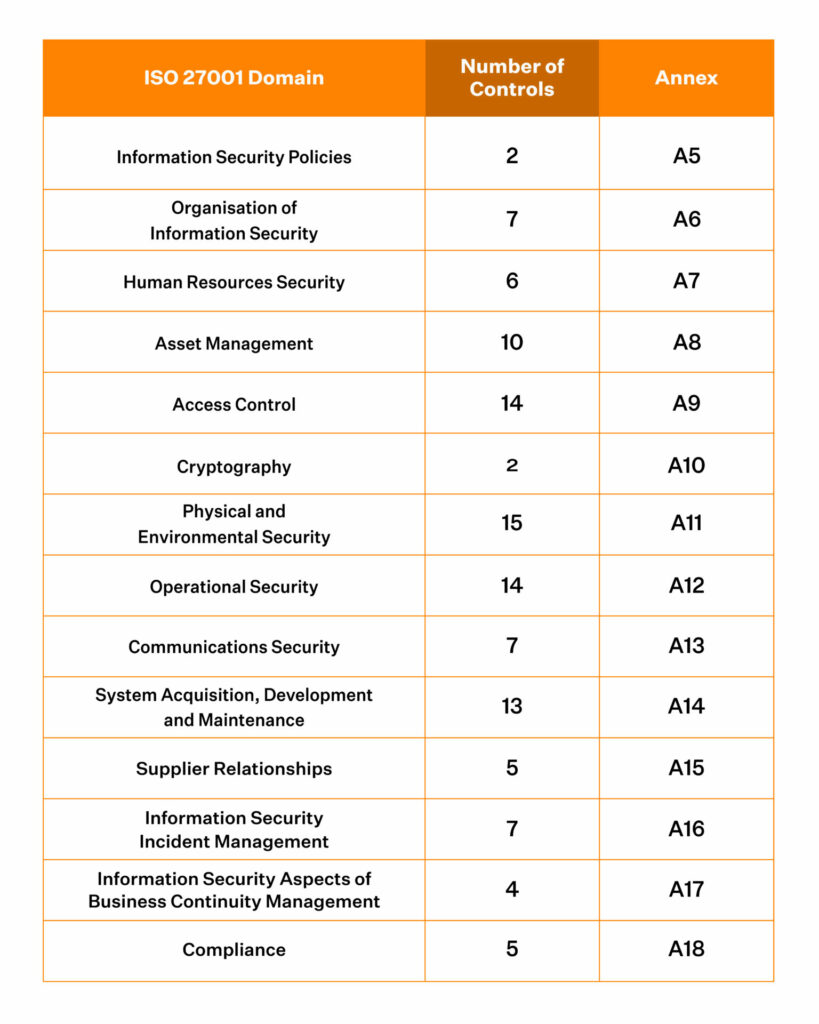
Guide to ISO 27001 Annex A Controls (Updated) Sprinto
Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month An access control policy defines how your organization manages user access to systems, data, and applications. Iso 27001 is a widely used security standard that lays out how to build an effective information security management system. Risk assessment24/7 soc 2 monitoring
An Access Control Policy Defines How Your Organization Manages User Access To Systems, Data, And Applications.
10k+ visitors in the past month Risk assessment24/7 soc 2 monitoring 10k+ visitors in the past month Iso 27001 is a widely used security standard that lays out how to build an effective information security management system.



![ISO 27001 Access Control Policy Ultimate Guide [+ template]](https://hightable.io/wp-content/uploads/2021/04/ISO27001-Access-Control-Policy-Template-Example-3.png)




![ISO 27001 Access Control Policy Ultimate Guide [+ template]](https://hightable.io/wp-content/uploads/2021/04/ISO27001-Access-Control-Policy-Template-Example-1-722x1024.png)