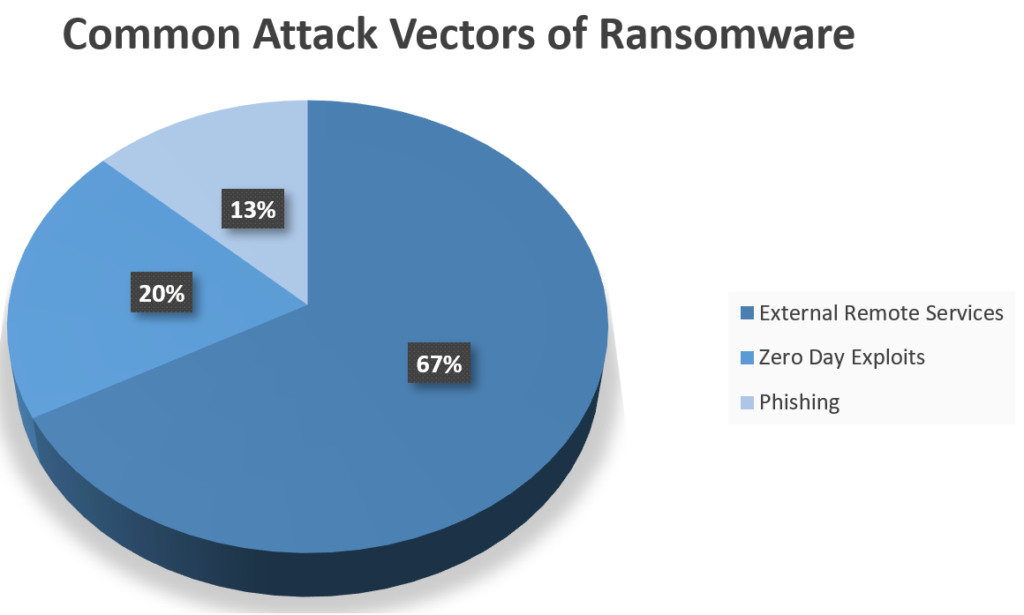
Recent Attacks On Networks - Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
Threat modeling explained A process for anticipating cyber attacks
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
Cyber Attacks Network Attacks Threats Vulnerabilities ⋆ IpCisco
Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an. Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom.
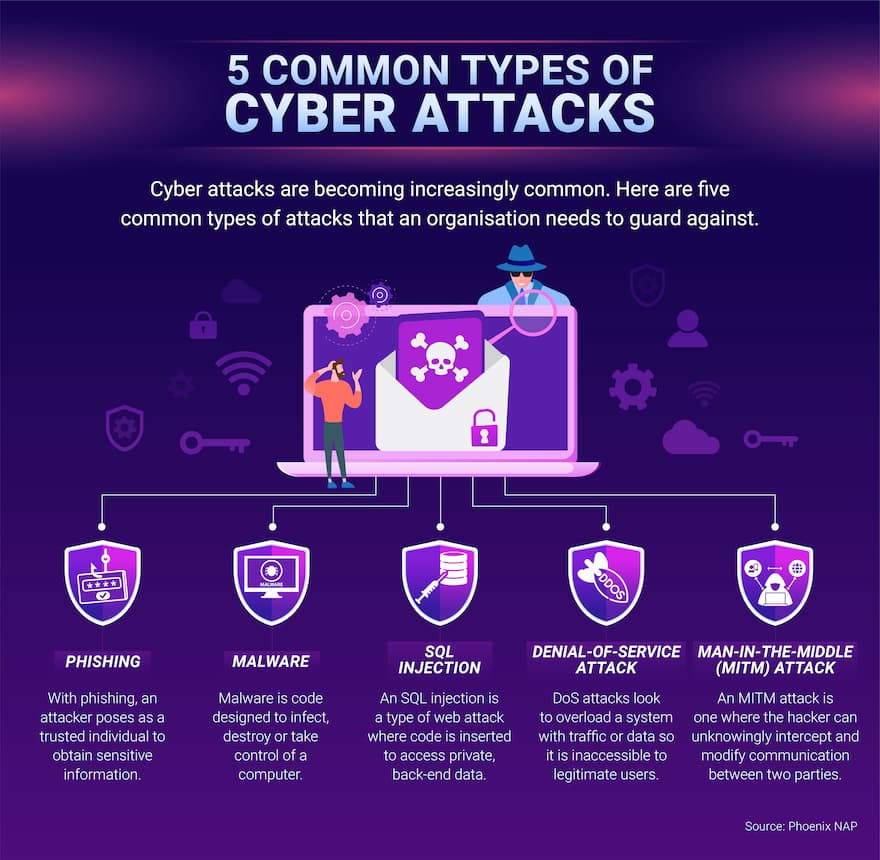
What is a Cyber Attack? Types, Effects & Prevention
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
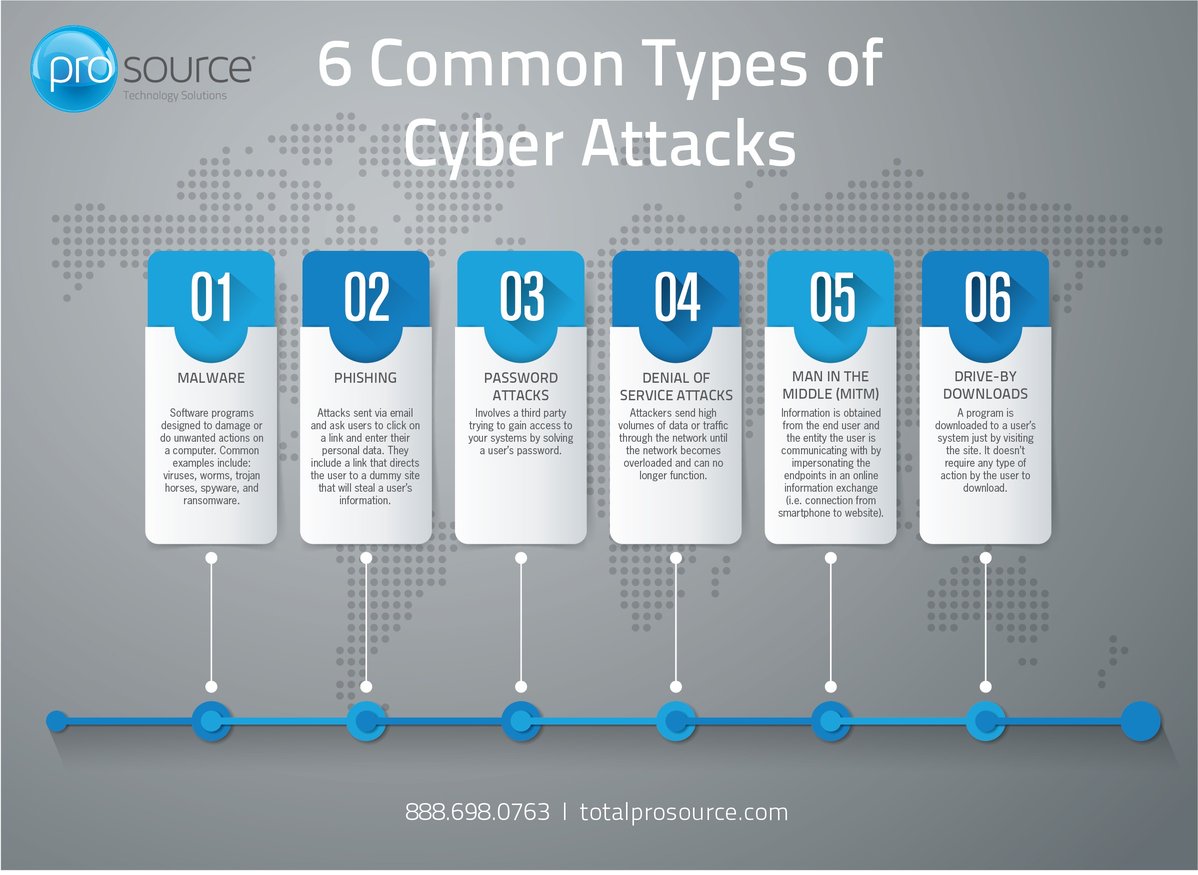
6 Common Types of Cyber Attacks
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
IoT Security
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
Cyber Attacks Tips for Protecting Your Organisation ECU Online
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
These are the top cybersecurity trends to watch out for in 2020 World
Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom. Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.
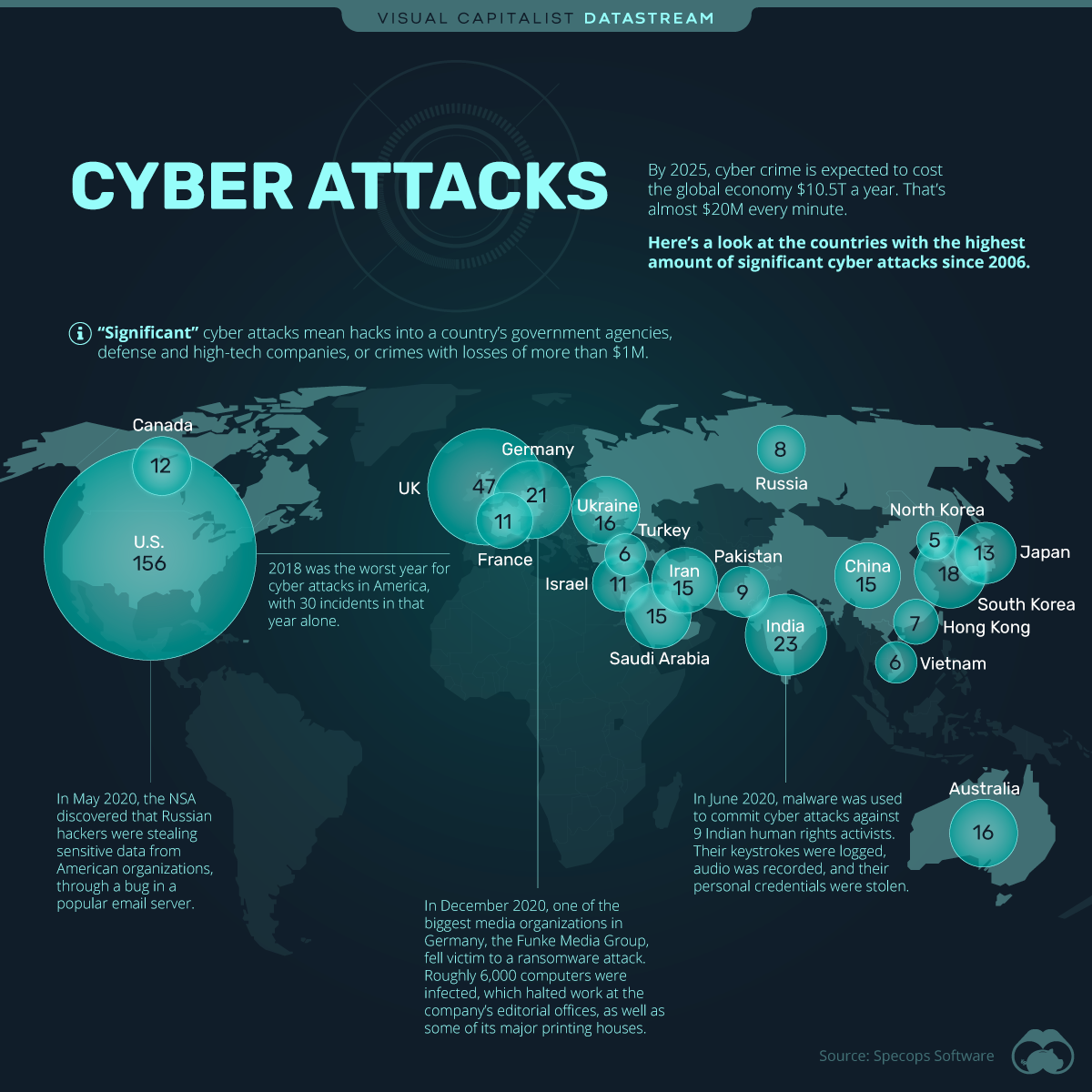
Ranked The Most Significant Cyber Attacks from 20062020, by Country
Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an. Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom.
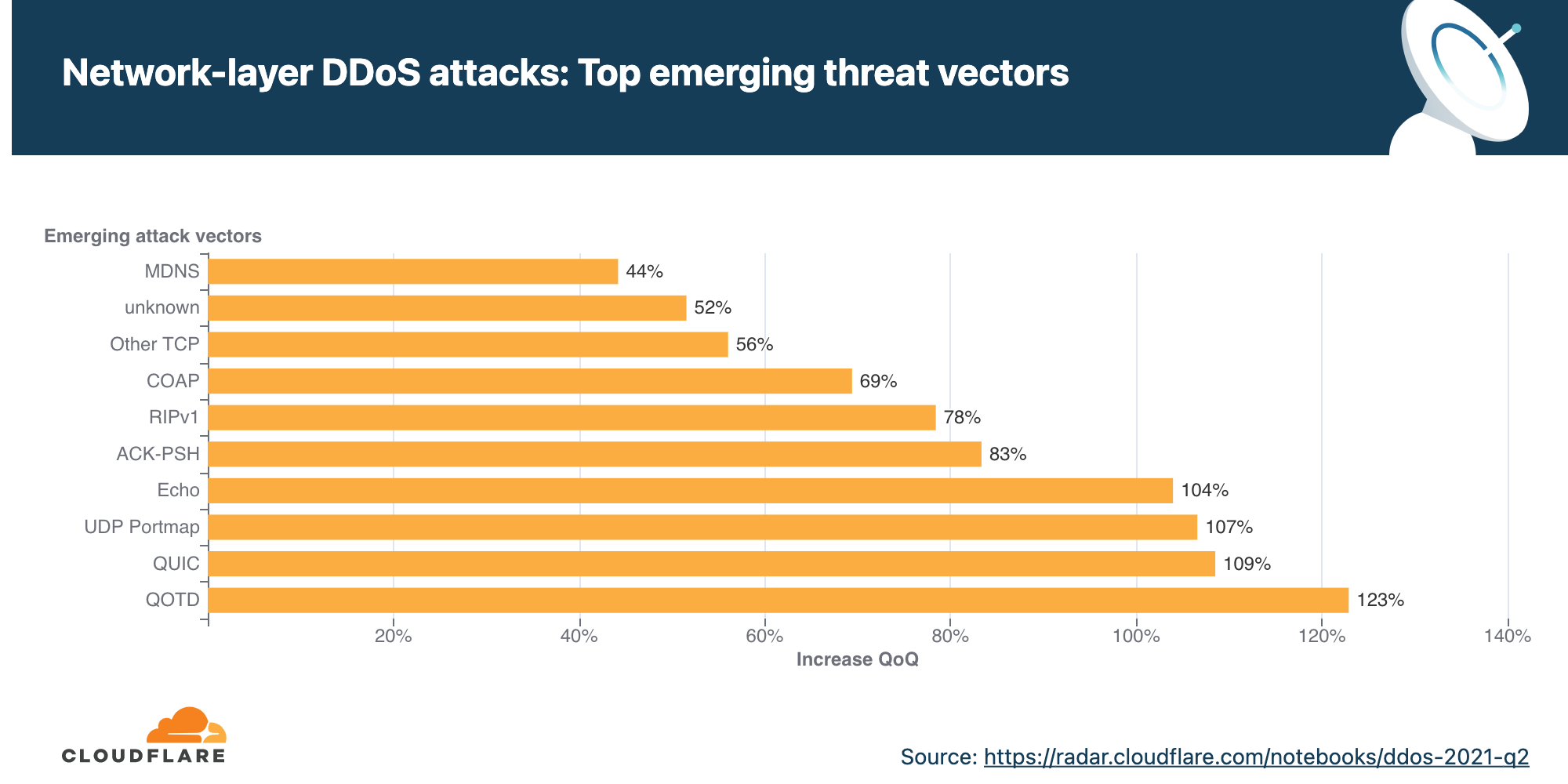
DDoS attack trends for 2021 Q2 All About Security Das OnlineMagazin
Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an. Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom.
2022 Ransomware Attack Trend Report Key Findings StoneFly
Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an. Cybersecurity news headlines in 2024 also included china hacking multiple major telecom companies, the largest ransom.
Cybersecurity News Headlines In 2024 Also Included China Hacking Multiple Major Telecom Companies, The Largest Ransom.
Kaspersky said it observed an unidentified threat actor gaining initial access to a running containerized infrastructure by exploiting an.